Description
The Duo service is leveraged in two different ways to trick people into providing login information and/or Duo passcodes:
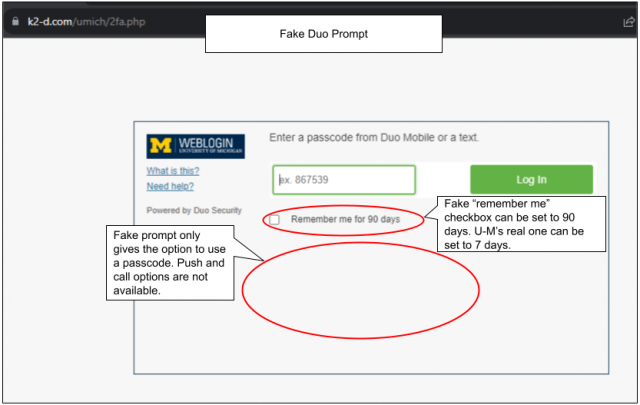
- A threat actor uses a fake login page to capture a person’s login information. The fake login then leads to a fake Duo prompt, specifically asking for a passcode. If the person then enters a Duo passcode (or passcodes), they can be used, along with the stolen login information, to access accounts fraudulently.
- An unexpected Duo push is sent to a person when they are not trying to log in. In this situation, a threat actor has used their stolen login information to log in to their account and is attempting to use Duo to complete the multi-factor authentication. If the person clicks “Approve”, the threat actor will be able to access their account. Pushes may occur repeatedly and persistently, trying to get the person to approve -- capitalizing on multi-factor authorization fatigue.
How to Protect Yourself
Do not assume that multi-factor authorization prompts sent using legitimate services are legitimate in their intentions. Pay attention to the details and look for red flags such as:
- You receive a Duo prompt though you have not tried to log in to a service that uses it.
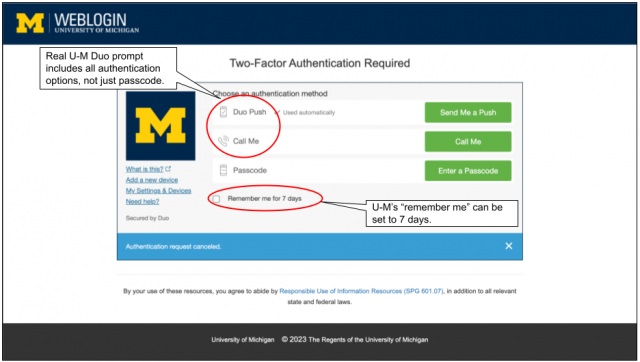
- Entering a passcode is the only authentication option offered. Legitimate Duo prompts offer more than one option.
- The “remember me” checkbox is a long duration, e.g. 90 days. U-M’s “remember me” can be set for 7 days.
- A scammer sends repeated Duo push notifications until you approve one. Don’t give in to pressure–deny them, report them as fraud, and change your UMICH (Level-1) password immediately! Paying attention to the location displayed on the Deny or Approve screen can help you identify when the approval is being requested by someone else in another location.
If You Entered a Duo Passcode
- Change your UMICH (Level-1) password immediately!
- Generate and use a new Duo passcode by logging in to an account that requires Duo and use a passcode for authorization. The passcode(s) you unintentionally gave to the threat actor will be invalidated when you create AND USE a new one. In other words, use of a later passcode invalidates passcodes created earlier.
- Be aware that you are not notified when a Duo passcode is used, so a threat actor could be using your passcode without your knowledge.
Report Suspicious Email or Request
Google at U-M users can forward phishing email to [email protected]; include what Google calls the original message. Michigan Medicine Outlook/Exchange users can use a Report Phishing button. For details, see Report Phishing & Email Abuse.
If You Get Caught
If you gave personal information in response to a phishing email or on a suspicious webpage, your account may be compromised.
- Change your UMICH (Level-1) password and follow the instructions at What to Do if Your Account is Compromised.
- Carefully review any online account that became vulnerable as a result of responding to the scam.