Description
In similar scams, a threat actor sends a document, e.g. “invoice”, through a legitimate service such as Paypal with instructions to call a telephone number for customer service assistance. If you call the number, they lure you into providing personal information under the guise of assisting you. They may ask to screen share with you online as another way to steal information.
How to Protect Yourself
- Be suspicious of emails sharing documents that you aren't expecting. If you aren't sure, contact the sender (preferably via text message, phone, or an alternate email address) and ask if they shared a document with you.
- Do not assume that emails sent using legitimate, secure services are legitimate in their intentions. These types of scam emails are not detectable by email scam filters because they are sent using legitimate services and the link that lures you into providing information is in a document.
- Pay attention to the details and look for red flags such as:
- The document is unexpected or it contains information you do not know about. It may also contain very little information. The purpose of the document is to get you to the next link – referred to as “laundering the link.”
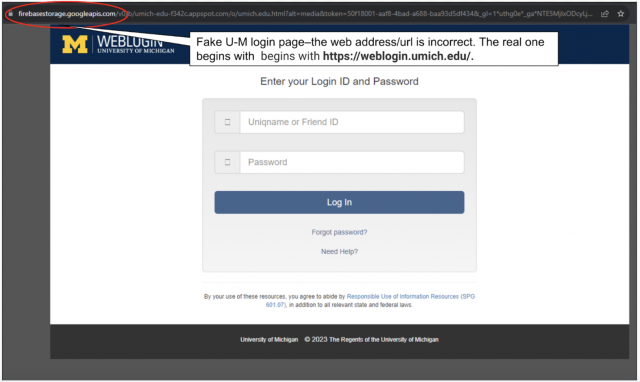
- If you access the document, it asks you to click a link to login with your credentials. Before entering your UMICH password on a web page, check that the page's web address/URL begins with https://weblogin.umich.edu/.
- If you access the document, it asks you to call a telephone number for further assistance. It is unusual for a legitimate service to only offer the option to call a telephone number.
- You are asked to screen share or download software. To verify the legitimacy of a request, you can end the call and contact the company or institution using its published contact information.
Report Suspicious Email
Google at U-M users can forward phishing email to [email protected]; include what Google calls the original message. Michigan Medicine Outlook/Exchange users can use a Report Phishing button. For details, see Report Phishing & Email Abuse. Report other suspicious requests or prompts by sending a description of your experience to [email protected].
If You Get Caught
If you gave personal information in response to a phishing email or on a suspicious webpage, your account may be compromised.
- Change your UMICH password and follow the instructions at What to Do if Your Account is Compromised.
- Carefully review any online account that became vulnerable as a result of responding to the email.