Check Chrome for pending updates
2/8/21 update: For the latest information about updating Chrome, see Google's Chrome keeps you up to date. According to Google, "Chrome checks for new updates regularly, and when an update is available, Chrome applies it automatically when you close and reopen the browser."
The information below was sent to the IT Security Community and Frontline Notify via email on December 4, 2018.
Please share this information with people in your units as appropriate.
Summary
Updates to Google Chrome normally happen in the background when you close and reopen Chrome. If you seldom close and reopen Chrome, you may be missing important security updates. Check the icon in the upper right corner of any Chrome window to see if updates are pending. If there are pending updates, install them.
Problem
Some Chrome updates require that you quit and reopen Chrome to take effect. People who go for long periods of time without closing Chrome may be missing important security updates. This leaves Chrome vulnerable to possible exploitation.
Affected Versions
Google Chrome web browser
Action Items
Check for pending updates. If you leave your Chrome web browser open for long periods of time (a week or more), periodically check the icon in the upper right corner to see if updates are pending:
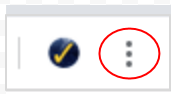
Three dots: No updates pending that require a Chrome restart.
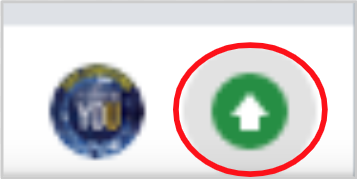 Green arrow: An update requiring a Chrome restart has been available for two days
Green arrow: An update requiring a Chrome restart has been available for two days
 Orange arrow: An update requiring a Chrome restart has been available for four days.
Orange arrow: An update requiring a Chrome restart has been available for four days.
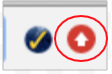 Red arrow: An update requiring a Chrome restart has been available for seven days.
Red arrow: An update requiring a Chrome restart has been available for seven days.
Install pending updates. Click the green, orange, or red arrow. Then, from the pop-up menu that appears, select Update Google Chrome.
In general, the best protection for your devices is this: keep your software and apps up-to-date, do not click suspicious links in email, do not open shared documents or email attachments unless you are expecting them and trust the person who sent them, and only use secure, trusted networks.
References
- Update Google Chrome (Google Chrome Help)
- A Vulnerability in Google Chrome Could Allow for Arbitrary Code Execution (Center for Internet Security, 11/21/18)
- Multiple Vulnerabilities in Google Chrome Could Allow for Arbitrary Code Execution (Center for Internet Security, 10/16/18)
