Description
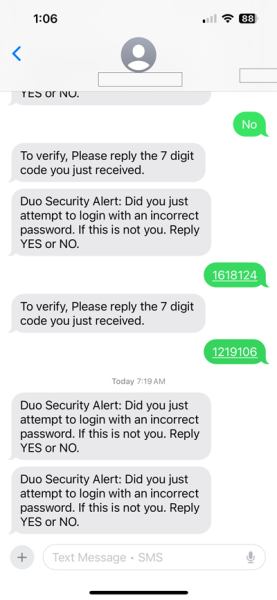
A threat actor may impersonate Duo in text messages in order to induce a person to provide Duo passcodes so that they can access the person’s account for malicious purposes. Prior to sending a person text messages to steal Duo passcodes, the threat actor has already stolen a user’s UMICH login credentials and mobile number (possibly through a fake login page or other phishing scam).
How it Works
- When the threat actor enters the stolen UMICH credentials to attempt to access the account, a Duo multi-factor authentication push notification is initiated.
- If it is not approved, the threat actor then sends a text to the user’s mobile number, impersonating Duo, asking if they attempted to log in.
- If/when the user responds NO, the threat actor initiates a Duo SMS passcode challenge to the user, and follows up with a text, impersonating Duo, that asks the user to confirm by entering the Duo passcode that was sent to them.
- If the user provides the Duo passcode to the threat actor, they can gain access to the account and may use it for malicious purposes, such as changing the direct deposit information.
Note: The threat actor may repeat the text requesting a passcode multiple times because some actions, like a change in direct deposit, requires multiple multi-factor authentications to perform.
For information and to learn how to protect yourself, see Multi-factor Authentication Scams.